S-MOBILE: Security of software and services for mobile systems |
Introduction
The objective of S-MOBILE is to create a framework and technological
solutions for trusted deployment and execution of communicating mobile
applications in heterogeneous environments. S-MOBILE would enable the opening of the software market of nomadic devices (from smart phones to PDA) to trusted third party applications beyond the sandbox model, without compromising security and privacy requirements.
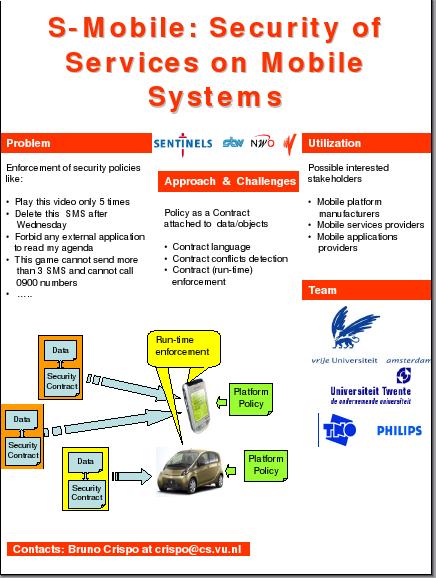
S-MOBILE Project poster.The problemIn the coming years, quantity and quality of e-services for and on mobile devices will increase creating a great business opportunity for services and applications developers. Already now, many people utilize over the air services for pre-provisioned services such as e-mail, schedule and contact synchronization. Mobile devices will become more powerful (a smart phone has more computing power than a PC of 15 years ago), so that smart-phones will become common shared platforms to run different applications. In such dynamic environment, key to success will be the ability to minimise time-to-market for flexible and yet secure services/applications. The above situation is essentially unsatisfactory because the current security model for applications running on mobile phones is based on trust relationships. Currently, a certification authority certifies an applications’ developer; to run the application, one must trust the certification. Different trusts domains segregate applications into sandboxes: interoperability is either total or not existing. E.g. if a payment service is available on the platform and an application for paying parking meters is loaded, the user cannot block the application from performing large payments. Further, as the security configuration of a mobile device is limited, its granularity is coarse: configuration may require upgrading the software or operator’s permission; an application can be denied network access, but it cannot be denied access to a specific protocol, or to a specific domain. In a nutshell, users (even corporate users) cannot configure their own security and privacy needs for mobile applications and platform they use. Further, the need of a trust relationships to deliver a service is a major cost barrier for independent developers. It also potentially increases the liability of operators (acting as root of trust) for the software running on their devices.
|
Project goalAim of this project is to provide technological solutions to improve flexibility on which policies users can choose or specify and consequently allow third party developers to freely develop applications and services and still mantaining or even improving the level of security required today by TLC operators. To achieve this, a contract-based security mechanism will lie at the core of the framework. A contract is a claim by a mobile application on the interaction with relevant security and privacy features of a mobile platform. This contract should be published by applications, understood by devices and all stakeholders (users, mobile operators, developers, platform developers, etc.). The contract should be enforced during development, at time of delivery and loading, and during execution of the application by the mobile platform. The new paradigm will not replace, but enhance today’s security mechanism, and will provide a flexible, simple and scalable security and privacy protection mechanism for future mobile systems. It will allow a network operator and a user to decide what an application is allowed to do, prevent bad code from running, and allow good code to be easily designed and deployed. UtilisationThis project addresses one of the key challenges related to the development of an open platform in an ambient environment. The project is expected to give insight into the evolution of the mobile platform and its future requirements and provide breakthrough solutions to the problem area that can be adopted inside existing products. Within the project, we provide prototypes and proof of concepts of all the new results we deliver. Emphasis will be given also to limit the impact on the usability of all these new mechanisms. Direct users of the S-mobile solution will be software developers, CE manufacturers and companies involved in offering services for mobile devices. The contract-based security mechanism proposed in this project will provide a way to enforce fine-grained security policies which can be agreed upon by both the service provider and its customers, with the consequences that service developers can better customize their offer to their customers. The results of S-Mobile will also contribute to streamline the development of secure application for mobile devices by offering a framework of reference for the security requirements throughout the application development. FundingThe S-Mobile project is currently in the startup phase. Funding for
the project has been obtained through the
SENTINELS research programme.
Project teamResearch institutes.
Industrial partners. Contact informationFor further information please contact:Bruno Crispo Email: crispo@cs.vu.nl phone: +31 20 5987829
| ||
Useful LinksPROJECTS WITHIN S-MOBILE:CRePE - Context-Related Policy Enforcing on Android Mobile Platform. OTHER RELATED PROJECTS: Mobile Phone Security. The Grey Project - Formal techniques for proving authorization. Tor on Android. Consequence Project - Context-aware data-centric information Sharing. RELATED FORUMS: Android Security Discussions. Mobey Forum - Mobile financial services. |
Publications: |
| - Bruno P.S. Rocha, Sruthi Bandhakavi, Jerry den Hartog, William H. Winsborough, Sandro Etalle. Towards Static Flow-based Declassification for Legacy and Untrusted Programs. In Proceedings of the 31st IEEE Symposium on Security and Privacy (S&P 2010), to appear, Oakland, CA, USA, May 16 - 19, 2010. |
| - Mauro Conti, Vu Thien Nga Nguyen, and Bruno Crispo. CRePE: Context-Related Policy Enforcement for Android. In Proceedings of the Thirteen Information Security Conference (ISC 2010), to appear, Boca Raton, FL, USA, October 25 - 28, 2010. [CRePE Demo Video] |
Last Revision: 2009/28/10 - Maintained by Mauro Conti
Email: mconti@few.vu.nl