The implementation is carried out on GNU/Linux (i486) platform with gcc-3.3.5, OpenSSL 0.9.7e library for cryptographic primitives (without any external cryptographic acceleration) and numerical analysis. To get a fair computational estimation, we did not use any code optimization of gcc while building our executables.
#include "clock.h" void start_counter(); /* Starts the counter */ double get_counter(); /* Returns: Number of cycles since last call to start_counter */
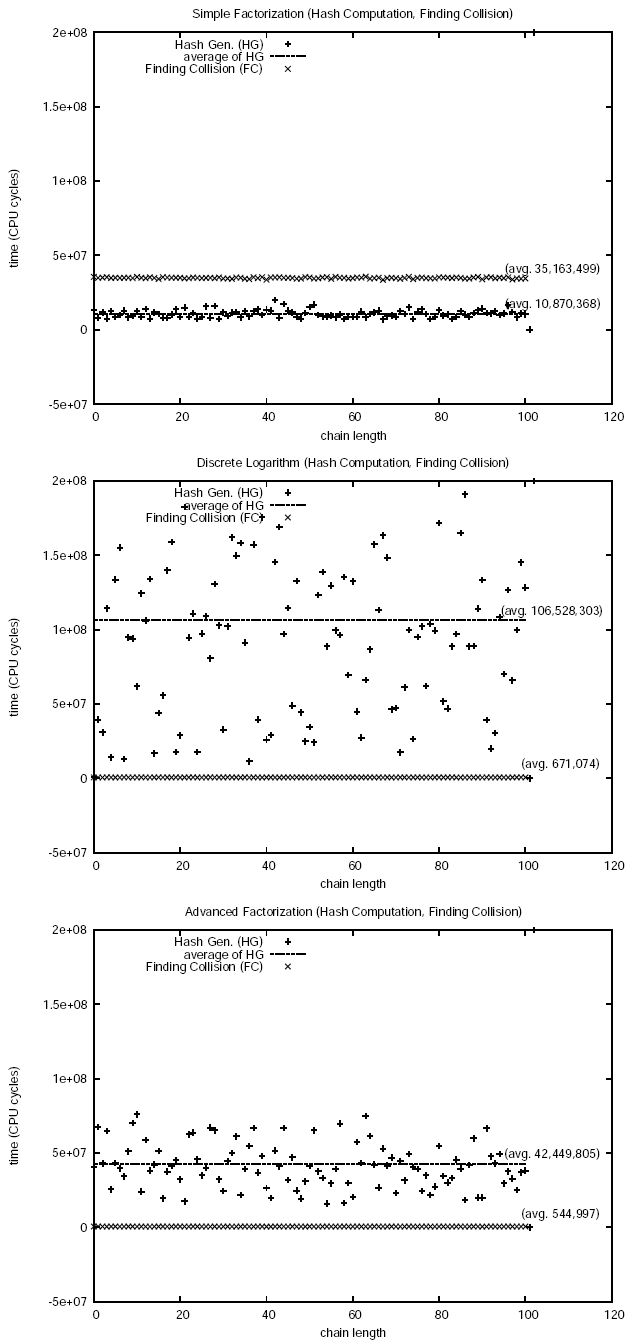
To verify the precision of this approach we marked the counter before and after sleep(sleeptime); function call (where sleeptime equals to one). We obtained 756,154,624.0 as return value (i.e., 756.2 MHz). We run each function of our interest for 101 times and discarded the first value of execution time in favor of cache warming process. Furthermore, results are gathered in run-level 1; to minimize interference from other processes. To plot all the results into graphs with common scale, we introduced dummy 101st and 102nd entries in our results with values equal to -1 and 200,000,000 respectively.
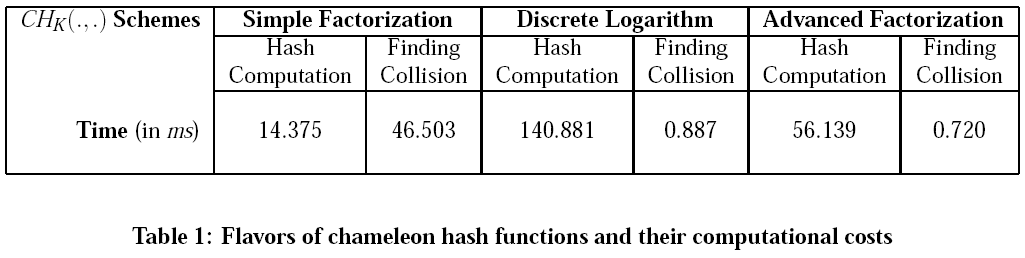
We implemented Chameleon scheme with three different methods, namely: Simple Factorization (SF), Discrete Logarithm (DL) [Chameleon Hashing and Signatures], and Advanced Factorization (AF) [Improved Online/Offline Signature Schemes]. Implementation of these schemes can be categorized into two phases: Hash Generation (HG) and Finding Collision (FC). These schemes produce hash of length 160-bits. Our results are summarized in the graphs shown in the Figure and Table shown below. The results provided in the following Table , for chameleon implementations, are the averages taken over 100 runs each.